The state of cyber security in 2019: A half-year retrospective
By Sam Bocetta For most of North America, approaching the middle of the year means going on summer vacation, preparing for the Atlantic hurricane season and enjoying warmer weather. For many information security specialists, the half-year mark involves looking at how cyber threats have unfolded since January and detecting patterns that may suggest the direction that […]

By Sam Bocetta
For most of North America, approaching the middle of the year means going on summer vacation, preparing for the Atlantic hurricane season and enjoying warmer weather.
For many information security specialists, the half-year mark involves looking at how cyber threats have unfolded since January and detecting patterns that may suggest the direction that cybercrime groups are headed in the near future.
The executive summaries in this regard have grown repetitive with expressions such as “cyber risks are rising dramatically” and “the entire internet has become an attack surface.”
There is some truth in these observations.
Threat level
If we were to use a line graph to plot the state of cyber threats over the last few months, it would look like the chart of a tech stock skyrocketing on Wall Street. We would get a similar result if we extended our plot points over the last few years.
In May 2019, the Irish government decided that its national information security needed to be revamped; to this effect, researchers from companies such as McAfee, IBM, HP, and Qualcomm gathered at the Cork Institute of Technology to launch the Cyber Ireland initiative. During the meeting, a troubling projection was discussed: at the current pace, the value of the global cybercrime economy will be higher than $5 trillion by the year 2021.
That means that cybercrime would represent roughly 10 percent of the global economy. What is interesting about this forecast is that the size of the global shadow economy (which includes black market transactions and traditional crime activity) is also 10 percent, meaning that cybercrime now runs parallel to it.
Cybercrime: The new cartels and mafia
Before we start showcasing new attacks, exploits, and cyber security threats for 2019, it is worth noting that cybercrime is an unstoppable force. The days of hackers proving their IT skills by means of breaching government and corporate networks have been over for a while.
One of the challenges of combating cybercrime is the involvement of government actors. Major cybercrime cartels actively recruited former intelligence agents, leading to major breaches such as the scandalous leak of cyber weapons developed by the United States National Security Agency a couple of years ago.
The U.S. Army now attends DEF CON Hacking Conferences, which are infosec gatherings, but who’s to say that soldiers formerly assigned to the 781st Military Intelligence Battalion will never join cybercrime groups? It certainly pays better than the military. In some cases, all it takes is a wrongfully discharged veteran to put his or her IT skills to work for a malicious hacking organization.
Cyberattacks don’t just happen at the state level, though. Small to medium businesses are frequently the target of attack, putting their customer data at risk. Case in point: a FireEye report published in February found that many low-quality, ostensibly “free” hosting companies were subject to a widespread DNS hijacking attack. The attack affected hundreds of domains belonging to telecommunications and internet infrastructure businesses.

With all the above in mind, here are a few rising cyber threats to look out for in 2019:
Ransomware
Remember the WannaCry ransomware attacks of 2017? The ones that brought down entire government agencies as well as the servers of major corporations such as Hitachi, Movistar, Boeing, and Renault? As of May 2019, these attacks are still targeting major organizations such as the official networks of municipalities in Georgia, Maryland, and Massachusetts.
Public school systems are also being affected, and the combined losses are in the millions of dollars. What we know about these attacks is that they were conducted with the EternalBlue exploit developed by the NSA and leaked in 2017. This attack targets the Microsoft Windows Server Message Block, which the company released a patch for even before the first round of WannaCry attacks three years ago.
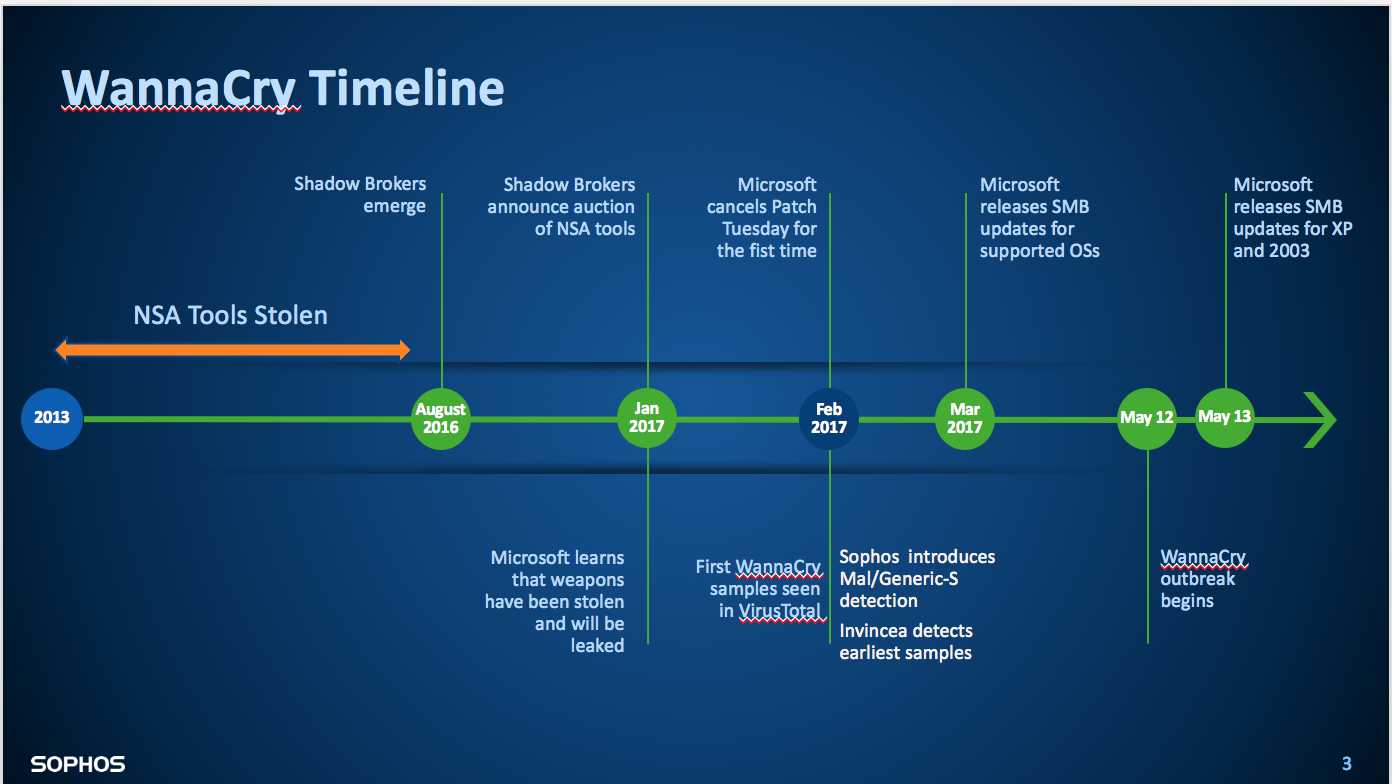
There are important lessons to learn about the prevalence of WannaCry attacks. First, ransomware attacks maliciously encrypt all files and folders before users are directed to make ransom payments for decryption, but these situations can be significantly mitigated with a solid data backup and recovery solution.
Second, failure to accept and install Windows security patches and upgrades can be disastrous.
Phishing and cyber squatting
Luring potential victims to fake websites that look legitimate has become a problematic cyber attack. Security experts now recommend that domain owners be more proactive in terms of providing some level of security to their visitors.
Cyber squatting, the insidious practice of registering misspelled or similar domain names for malicious purposes, can be mitigated through domain security services.

Beyond the safety of visitors, domain name owners should also think about potential damage to their online reputation, something that has become a priority for many brands that strongly rely on the internet as their main business platform. Name.com offers strong security services for customers who purchase a domain or hosting on the site, in strong contrast to the weak security policies by many other domain registrars.
The Plead backdoor malware
This is an example of high-level malware mostly used for corporate espionage, but many small business owners have been hit with this malware because they are ASUS WebStorage customers. Once the Plead backdoor is installed on a computing device, it allows remote code execution.
Information security researchers from ESET have determined that Plead malware is being dropped by man-in-the-middle (MitM) attacks, particularly at the router level. What this means is that hackers are intercepting login data from devices connected to certain wireless routers before dropping the malicious payload. Once this happens, the attackers wait for a connection to ASUS WebStorage, a cloud computing service, before completing the attack.
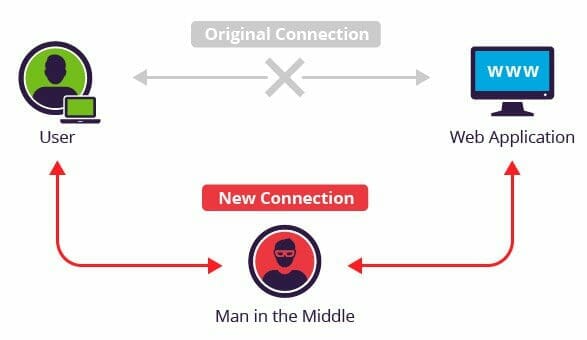
In this case, the best practice to lessen the risk of MitM attacks is through the use of virtual private networking (VPN) technology. The best VPNs today use a mix of cutting edge encryption protocols, such as OpenVPN, which secure your internet connection so that hackers cannot decipher username/password combinations even if they are monitoring a device.
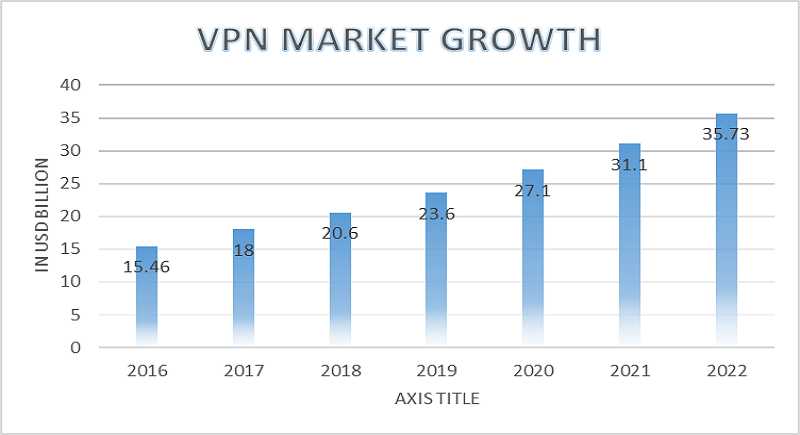
When you’re connected to the internet through a VPN, all of your browsing data (traffic) passes through this encrypted “tunnel”. So, even if you end up visiting a site that is not HTTPS-secured, you’ll have a good defense against MitM attacks. In 2018, nearly a quarter of all internet users connected via VPN. This is a positive trend that is bound to continue.
The bottom line
In the end, the state of cyber security in the middle of 2019 is not looking any better (unless you’re a hacker) than it did at the beginning of the year, and it is unrealistic to think that will change over the next six months. Your best protection against modern cyber threats is to follow recommended practices and to think about mitigation as well as prevention.
With the threat level where it is, the chances are good that a hacker will wiggle through your defenses eventually. At that point it becomes a matter of minimizing the damage and recovering from the fall out. One under-suggested tactic that should help is to follow a cybersecurity blog or two to stay current on zero-day exploits and the changing landscape of popular malware methods as they happen.
Sam Bocetta is a freelance journalist specializing in U.S. diplomacy and national security, with emphases on technology trends in cyberwarfare, cyberdefense, and cryptography.
